With data breaches extracting millions in damages and eroding customer trust, Azure DevOps consultants prioritize security as a cornerstone of application modernization.
Yet bolting compliance controls reactively proves complex, costly, and ultimately futile.
True defense demands infusing security intrinsically across the entire software lifecycle.
Microsoft Azure DevOps provides a robust set of capabilities purpose-built to engineer resiliency into applications proactively.
This post explores key Azure DevOps security services enabling developers, testers, and operators to collaboratively design, validate and monitor secure applications at enterprise scale.
By natively integrating defenses spanning infrastructure, data, and access, teams can ship code confidently knowing security stays embedded by design.
Automating Infrastructure Protection
Infrastructure as Code (IaC) techniques allow instantly spinning up preconfigured, compliance-ready environments from versioned templates.
- Apply pre-approved network security groups, firewalls, and endpoint controls through IaC templates.
- Scan provisioned resources for misconfigurations causing vulnerabilities.
- Destroy sandbox environments automatically after code validations to minimize attack surfaces.
- Enforce role-based access assigning only necessary permissions.
- Mask secrets and credentials, using automated rotations.
- Receive alerts for suspicious admin activities or resource usage spikes.
With programmatic infrastructure hardening, consistency guarantees environments remain secure despite frequent provisioning.
Embedding Data Safeguards

Transparent data protections start right within code repositories:
- Classify data types (PII, financials, IP) to apply appropriate handling policies.
- Redact sensitive details before committing source code.
- Prevent leaks by restricting repository access to authorized teams.
- Mask data in non-production environments.
- Analyze code commits to identify new data flows for review.
- Validate handling against regulatory compliance requirements.
- Monitor data usage and transfer trends for anomalies.
- Generate inventory reports detailing data locations across services.
Encoding data governance practices directly into engineering workflows embeds privacy by design versus obscurity.
Enabling Secure Collaboration
With globally dispersed teams, thoughtfully managing access and collaboration is crucial:
- Integrate repository permissions with centralized identity providers.
- Grant temporary credentials to outside contributors expiring once work is completed.
- Require multi-factor authentication for production data or infrastructure access.
- Automatically revoke credentials after employee offboarding.
- Restrict service accounts to solely needed resources.
- Mask confidential data in shared pipelines and test logs.
- Route tasks to authorized internal teams to handle them securely.
- Log and audit activity across all repositories and environments.
Smart access controls balance open collaboration with governance safeguards befitting untrusted networks.
Automating Policy Enforcement
Repeatable pipeline workflows allow preventative policy enforcement:
- Scan source code for vulnerabilities or license conflicts upon commit.
- Validate that environment configurations match security benchmarks.
- Check user identities and test assets before pipeline execution.
- Block unapproved tasks like unmasking secrets or uncontrolled deployments.
- Disable unnecessary functionality and ports by policy.
- Mandate peer reviews for impactful modifications.
- Prevent check-in of non-compliant changes through gating.
- Rollback pipelines if vulnerabilities emerge post-deployment.
Enabling Preventative Testing
Expanding test coverage beyond functional validation is pivotal:
- Inject failure scenarios simulating component outages or corrupted data.
- Fuzz test interfaces with unexpected inputs probing for weaknesses.
- Attack surface reviews scrutinize exposed endpoints and permissions.
- Volume test for performance degradation indicative of denial of service vulnerabilities.
- Bug bounties incentivize external ethical hackers to probe for flaws.
- Shift security is left in sprints to prioritize controls and attack simulations.
- Automate the creation of production-scale test datasets reflecting true sensitivity.
- Target regression testing on high-risk components prone to reintroduce old bugs.
Robust testing disciplines exercise vulnerabilities before attackers can exploit them post-production.
Monitoring for Threat Detection
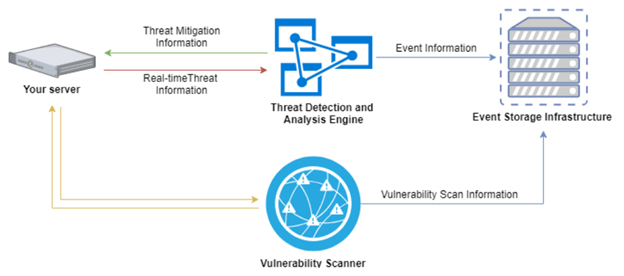
Runtime telemetry and analytics provide threat visibility:
- Ingest logs into SIEM systems correlating events for incident investigation.
- Analyze admin actions and permission changes for insider risks.
- Detect abnormal usage volumes indicative of data exfiltration.
- Correlate infrastructure metrics with user identities to audit access.
- Scan external attack surfaces for emerging exposures.
- Map dependencies to quantify impact radius from component compromises.
- Simulate attacks for blue team training on responsiveness.
- Cyber deception techniques confuse adversaries prowling internal networks.
- Threat intelligence integrations detect known bad actors and probing environments.
Empowering Developer Self-Service
Enabling developers to securely self-remediate boosts velocity:
- Embed security guidance into native workflows exposing best practices.
- Auto-generate fixes for insecure code patterns.
- Provide contextual training modules within IDE on secure coding.
- Automate the creation of pre-approved sandboxes for exploration.
- Supply guardrails preventing production deployments without approvals.
- Segment developer environments and permissions minimizing production access.
- Expose vulnerability data directly to engineers for refactoring prioritization.
- Orchestrate app penetration testing and remediation cycles seamlessly.
Promoting Collective Ownership
Expanding accountability across teams fosters security culture:
- Incorporate security needs from the outset in capability planning.
- Reward vulnerability discoveries and security enhancement ideas.
- Rotate team members through security-focused sprints.
- Gamify training with team security scoring to spark competitiveness.
- Crowdsource threat modeling to collectively probe risks.
- Encourage grassroots communities of practice to share lessons learned.
- Demand mandatory security reviews from other teams to bring outside perspectives.
- Capture and share post-mortems on past incidents company-wide.
Holistic security ambassadors drive culture shifts that no single team can accomplish alone.
Maintaining Guardrails Over Time
Sustaining secure engineering demands continuous investments:
- Refresh controls to address emerging attack categories like deep fakes.
- Updated training ensures developers recognize new social engineering techniques.
- Evolve tools keeping pace with open source security innovations.
- Diligently patch platforms and dependencies promptly.
- Insulate downstream systems from third-party risks with encapsulation.
- Segment particularly sensitive data and code even internally.
- Obtain independent validations to complement internal testing.
- Balance legacy maintenance needs with proactively modernizing vulnerable legacy systems.
Azure DevOps capabilities compound atop robust Azure security foundations spanning identity, networks, data, infrastructure, and intelligence.
Automating Security Compliance Checks
Embedding controls directly into native developer workflows promotes consistent compliance across the lifecycle:
- Block pipeline execution if scans reveal new high-severity flaws.
- Enforce mandatory fixes for critical vulnerabilities before the code moves to staging environments.
- Run penetration tests mimicking real attacks to obtain independent validations.
- Continuously monitor controls and attack surfaces to identify compliance drift.
- Generate audit trails demonstrating rigorous compliance to auditors.
- Integrate security sign-offs from designated owners to approve releases.
- Automate evidence collection for certification renewals minimizing audit overhead.
- Notify responsible developers of failing checks blocking pipelines.
By codifying and automating security checks natively in the toolchain, compliance becomes an intrinsic byproduct of delivery rather than an afterthought.
Securing the Interface Attack Surface
Validating the UI and API security is pivotal since these interfaces represent the primary customer attack surface:
- Perform extensive abuse testing with invalid, unexpected, and unauthorized inputs.
- Analyze UI widget permissions ensuring consistency with access rules.
- Confirm form field validation stops malformed submissions.
- Check for information disclosure in error messages.
- Confirm API secrets and keys employ short-lived, encrypted tokens.
- Scan JavaScript dependencies for vulnerable libraries.
- Test administrative interfaces with reduced permissions for missed controls.
- Perform source code reviews on UI and API logic for holes.
- Engage external bounty hunters to find flaws a familiar internal eye may miss.
Enhancing Operational Security Posture
Secure deployment and operations require controls spanning technology, processes, and people:
- Restrict production access only to essential personnel using just-in-time, time-bound credentials.
- Scrutinize admin activities through behavior analysis for anomalies suggestive of insider threats.
- Institute mandatory peer code reviews for high-risk operational changes.
- Require testing on staging environments matching production scale to validate controls.
- Implement change control boards to govern and audit impactful modifications.
- Limit visibility into secrets and credentials through masking. Rotate periodically.
- Disable unneeded functionality and open ports by default through whitelisting policies.
- Partition production data in secured zones with no Dev/Test access.
- Validate disaster recovery procedures through failure simulations.
- Monitor all administrator actions via irrefutable logging for forensic audits.
- Institute mandatory security training for all personnel with environmental access.
You should consider hiring Azure DevOps consultants to formally certify operational controls through independent audits.
Maturing operations practices brings discipline commensurate with online threats targeting mission-critical cloud infrastructure.
Together these layers drive security intrinsically into workflows and culture – avoiding the pitfalls of peripheral bolt-on controls.
How do you plan to include security into your DevOps procedures earlier and more consistently?
What new methods or capacities spark your interest? Let’s continue the conversation down below!





